iOS 10.2 encryption: fully supported

Apple has released 7 beta versions following the official iOS 10 launch in September. A significant security flaw which affected local iPhone backups was detected and removed within 2 weeks. We noticed the security fix with the introduction of iOS 10.1 back in October. The news was covered in The Register:
In the mobile space, where consumer adoption has overtaken desktop technologies, frequent updates are crucial to ensuring the security and stability of widely used mobile platforms, including iOS. With cyberattacks becoming more sophisticated, the ongoing battle between tech giants and well-versed hackers lead to rising expectations from users for bug-free software being released publicly.
Media outlets have covered this security flaw topic extensively, given that iOS 10 is now used on more than 75% of all Apple devices.
As the app-data company, it is critical that we swiftly identify changes in backups introduced with new iOS updates in order to best serve our customers. We are committed to offering robust support for all features released, including encrypted iTunes and iCloud backups.
Our clients -- ranging from regular users to companies turning to mobile applications to stay in touch with customers -- rely on our product’s best-in-market functionality to recover encrypted backups for all iOS versions.
We are proud to announce that the iPhone Backup Extractor now fully supports encrypted local backups in the upcoming iOS 10.2.
What makes iOS 10.2 backups "uncrackable"?
The change is associated with a different key derivation process used for iTunes backup encryption than the one used previously. Finding the new derivation process was the missing piece to increase security to iTunes backups, and to being able to support this new feature in iPhone Backup Extractor, for our users.
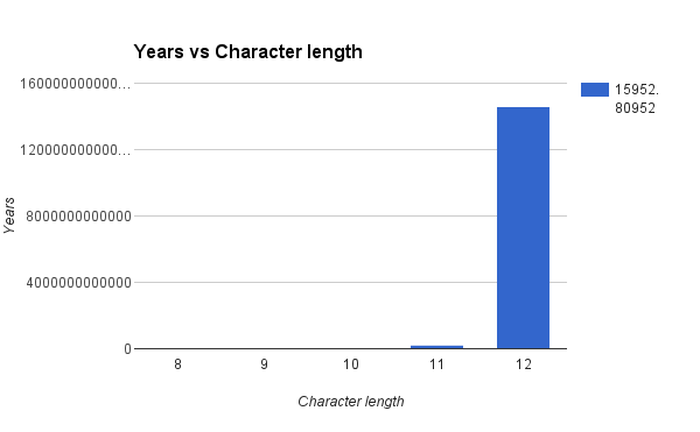
The encryption update included in iOS 10.2 removes the possibility for brute force attacks to be a viable option for hackers, because it takes significantly more time for each attempt to guess the backup password.
Our team estimated that it takes roughly 7 seconds for a password to be verified, before opening the backup, with a regular laptop CPU.
Why is this important to you?
Mac Forensics expert Sarah Edwards urges companies to improve and grow Mac skills, especially if there are dedicated security teams or professionals working on detecting and accurately responding to security incidents in due time. Security threats come from different directions, from phishing and scam emails to social engineering and using unencrypted connections.
Turning on encryption for iPhone backups is only one of the precautionary methods used to mitigate risk. As encryption is hardened in iOS 10.2, local backups are harder to retrieve by iOS data recovery tools available on the market.
The iPhone Backup Extractor is the only tool to date that provides support for iOS 10.2 encryption, allowing legitimate users to recover lost or deleted backup files.
Forensics examiners and investigators can also benefit from this feature directly, which is available with the most recent version of iPhone Backup Extractor.
Advocating for security
Encryption is now rightly the default for all iTunes backups, and users will need to manually turn it off if they wish to. Switching to a default encrypted state is an important move for Apple, marking a security-first approach, on top of adding extra features in iOS 10.
Reincubate is committed to keeping this momentum going, regularly releasing updates to both iPhone Backup Extractor and to the iCloud API, ensuring maximum compatibility with encryption changes.