Facebook store insecure authentication tokens in iPhone backups

Over the last month or so, a handful of iOS apps have been under the spotlight with regards to security weaknesses and iPhone tracking. Now it's Facebook's turn, although the issue in question applies to many other social network sites such as LinkedIn, Dropbox, and apps that use these sites to authenticate users on iOS.
Security researcher Gareth Wright found Facebook's iOS app keeps authentication tokens in a plain text file. Those tokens are equivalent to the password you use to log in.
Storing authentication tokens in a backup isn't necessarily a bad idea. After all, if you have to restore your phone from a backup, it's nice to see everything logged in as it was, and the token is necessary to do this. You can see how this works with Facebook's current implementation:
- Log in to the Facebook app on your iPhone, and back it up with iTunes
- Log out of the Facebook app on your iPhone (go to the bottom of the left menu and click
Settings→Log Out - Restore the iTunes backup to your phone
You'll see you're logged back in. Neat.
The road to hell is paved with good intentions
Whether Facebook stores its authentication token in the backup isn't the main issue. The biggest problem here is that the token isn't encrypted, doesn't have a device-specific element to it, and isn't time-limited. That means that someone could pull the file from your backup and import it to their own device. In simple terms, anyone who can access this file can have full access to your Facebook account and use it to steal your identity or track your activity.
In addition to this, many third-party apps and services use Facebook as an authentication service. If a hacker is already signed in to your Facebook account, they could also access these services using it.
Facebook has replied to news agencies with the following comment, although they seem to omit the likelihood of insecure backup hacking which we think is the easiest method.
Facebook's iOS and Android applications are only intended for use with the manufacture provided operating system, and access tokens are only vulnerable if they have modified their mobile OS (i.e. jailbroken iOS or modded Android) or have granted a malicious actor access to the physical device. We develop and test our application on an unmodified version of mobile operating systems and rely on the native protections as a foundation for development, deployment and security, all of which is compromised on a jailbroken device. As Apple states, "unauthorized modification of iOS could allow hackers to steal personal information ... or introduce malware or viruses." To protect themselves we recommend all users abstain from modifying their mobile OS to prevent any application instability or security issues.
Should you be worried? In order to get this file, the person must have physical access to your iOS device or a PC with an unencrypted stored backup. A casual hacker may not have access to those, but a determined one might be able to arrange such access.
Clearly, app publishers such as Facebook could help themselves with the following:
- Apply additional encryption to authentication tokens in backup
- Ensure the tokens have a device-specific element so that they cannot be used on other devices
- Set the tokens to have an expiry date in a near future
- Alert users to new logins to a service from restored tokens
Want to examine your own Facebook authentication token?
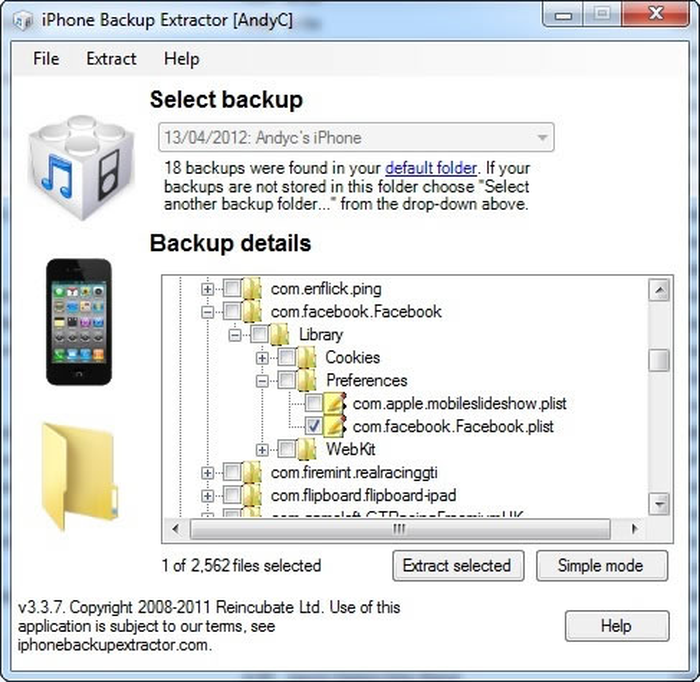
You can do this using iPhone Backup Extractor and accessing your backup in "Expert Mode". You won't be able to read the data or use it to sign into Facebook unless you know what you're doing -- and we've withheld publishing how to do this for security reasons -- but it doesn't take much to figure it out.

