iCloud photos and security in the spotlight
Unless you've been living under a rock for the past few days (in which case you've made a good decision in coming straight here), you'll undoubtedly have heard about the publication of many private photos from over a hundred different celebrities.
This breach in privacy is something that's been tied to iCloud, but it isn't entirely to blame. It has been made apparent that these photos have been collected for some time from numerous sources. Such a breach tends to lead to large prison sentences and no doubt the same will occur here, but I think many people are underestimating just how much data from iCloud was stolen.

What data does iCloud hold?
Here at Reincubate, we love giving people access to their data. After suffering data loss ourselves we know how much it means to get it back. In recent weeks we've been building and launching an API to pull down and parse your iCloud data (if your company might have a use for this kind of service, let's chat) so we know a thing or two about the excellent security that protects your data, as well as just what can be achieved by knowing the Apple-ID and password combination.
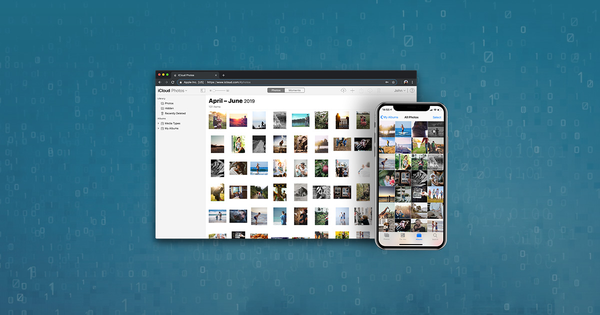
With your credentials in hand and iPhone Backup Extractor with iCloud functionality, you can extract your iPad or iPhone photos (as we all are now very aware), but you can also extract all your SMS data, contacts, app-specific information (WhatsApp etc) to only name a few! Furthermore, you'll have access to other iCloud functionality that isn't stored within the backup, things like tracking your iPhone's location or downloading the files you've stored within the iCloud, such as documents, calendar, bookmarks and more. Handy!
This is absolutely fantastic when you've lost your phone and are able to save those baby pictures, that business contact or that video of fluffy. While equally not so fantastic when this information is in the hands of a malicious third-party.
How was the data leaked?
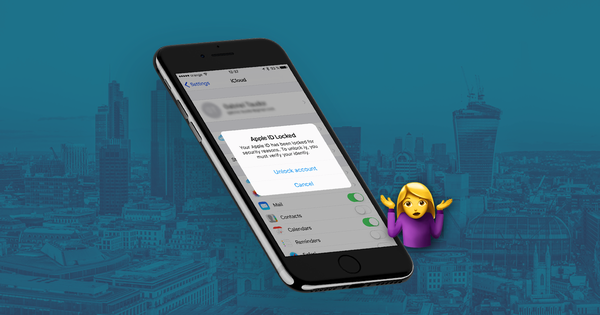
As mentioned above, you need the Apple-ID / username combination to access this data. There's no other way around it. (Unless of course you've got a team of world-class cryptographers performing novel mathematics to break the leading standard in encryption, but then you'd most likely have better things to be doing). Finding the Apple-ID of a user isn't easy for the vast majority of people, but remember this is just an email address and depending on your presence online, concealing your email can be difficult. While many people will use different passwords for different services (as well you should), we rarely use a different email address, so having discovered an email address used for one service it's not too great an intellectual leap to presume it will be correct for others.
So we're then left with the password which can be guessed or reset. Resetting the password requires either access to the email account or knowledge of the various secret questions that you have set - this information however can be difficult to come by. Guessing on the other hand requires literally no knowledge about the account owner! The natural response for any company serious about security then, is to make the guessing hard. If you have an Apple account you may remember the myriad of rules your password had to meet to be considered usable, which is the first technique used to make things harder for an attacker. No longer will access be granted thanks to the naïve user who sets their password as 123456, or the forever self-non-fulfilling changeme.
"OK great, we have strong (ish) passwords, now what?"
Well, the second portion of the problem is guessing lots of times. In this case, there are a couple of nice approaches. One is to make the procedure slow by either performing many thousands of hash iterations or by using a "slow" algorithm (this is a nice article talking about it in more depth, you know, if you're into that kind of thing). While this reduces the number of attempts that can be made per second, more can be done and in the majority of cases it is. We have multiple safeguards in place to ensure that brute forcing of accounts simply cannot be completed.
There are various techniques that can be implemented (log-in attempts can be monitored and accounts disabled if suspicious activity is found for example), but the problem in this case was that there was a log-in API that didn't have any additional protection. Attackers found that the Find My iPhone API would allow for any number of password attempts, meaning that they simply had to try a list of commonly used passwords, hoping that one of them worked.
That's it. It was that easy.
But not anymore, as soon as the flaw was revealed Apple punctually patched it. Apple takes a number of precautions to prevent unauthorized access to user data by third parties, but it is in your own duty to secure your data as well, be it with Apple's iCloud or other apps and services.