How to protect your iPhone, Photos, & iCloud account
In the US, iPhone users now make up around 45% of all smartphone users (as of January 2020), and almost a billion users store data with Apple’s iCloud. With such a huge amount of personal data available, hacking attempts are persistent, sophisticated, and indiscriminate.
This article has been created to help you protect your Apple devices and data from hackers. We’ve laid out the most effective methods to keep your devices and data safe, beginning with the essentials and moving on to more involved safety measures.
Since 2017, Apple have allowed "differential privacy" on iCloud user data. This function allows users to enable or disable data-sharing for analytical purposes. The same iOS 10.3 update also included numerous notifications promoting two-factor authentication (2FA) adoption. Both actions work to keep your iPhone data safer.
How can I protect my data?
Jennifer Lawrence, Kirsten Dunst and Kate Upton were among the victims of the notorious Celebgate hacking attacks, which accessed data from iCloud accounts remotely and without permission. Celebrity hacks show these breaches can happen to anyone, Apple already implements numerous safety and privacy protections as defaults (such as 2FA) to make sure your iOS devices and iCloud data is kept safe. Successful hacking attacks are almost always the result of users failing to implement Apple’s security tools properly or phishing.
You can use this article to ensure you’re making the most of Apple’s security features. First, we cover the 12 most important steps to protecting your data which we recommend every iCloud user follows. Once we've covered the essentials, we outline a further five safety measures which are slightly more advanced or involved. You may want to consider implementing these steps if you are at particular risk of being hacked, or if your data is particularly sensitive:
12 Easy safety measures everyone should always take to protect their iPhone, Photos, & iCloud data🔒
Let's start with the basics...
1. Beware of phishing attempts
Phishing messages are fake replicas of legitimate security measures. They're emails, text messages and calls you receive, claiming to be from Apple, Google or other trusted companies, and which usually contain urgent or time-sensitive messages, such as: "CLICK NOW to ensure your account stays active!" As these emails, messages and calls are designed to access personal information, they often ask for user credentials. These are all nonsense -- and dangerous to click on.
Be wary of any unexpected email, message or phone call asking you for personal details. Such an email might say something like: "We've recently detected suspicious activity in your iCloud account. Use this form to reset your password."
Whenever you see an email asking for credentials, check the URL. If you see any domain other than iCloud.com, or if you notice an insecure certificate when browsing, it's most likely a phishing attempt. Here's Apple's icloud.com, and the secure certificate that you should see on it:
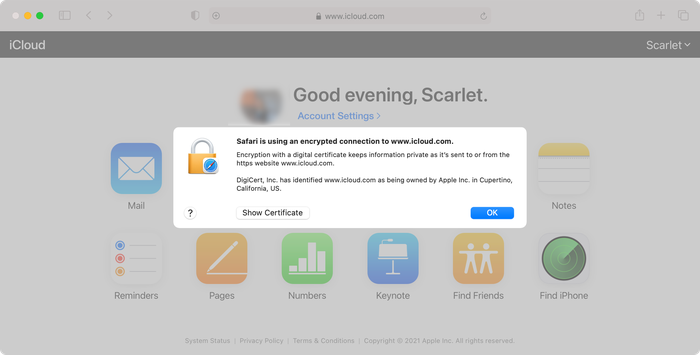
Messages and calls claiming to be from Apple are very unlikely to be authentic, as Apple is much more likely to contact you by sending a notification directly to your iOS device.
We recommend you always access your iCloud account manually, by opening in a new tab in your web browser and typing in "icloud.com", even if you think a message may be authentic. Always use the official iCloud site to log in, change a password, or check up on warning messages. You can also get in touch with Apple’s security team to report any phishing attempts to them.
Received a message you're really worried about? 😰 See our guide on what to do if you might have been hacked.
2. Keep your email address private
Every now and then, an exploit is discovered that can compromise your data simply through clicking a link.
Mike Murray, a security expert from Lookout, described the last such exploit as “the most sophisticated spyware package we have seen in the market”. It was linked with NSO Group, an Israeli company which makes security applications for governments. A few hours later, Apple launched an iOS update, which fixed this vulnerability.
What can we take from this? Even though the problem was solved rapidly, other security holes could be discovered. Having a private email address is a good way to avoid targeted or random spyware attacks in this way. Here are three things you can do to ensure privacy:
- Use a separate email address for purchases, social networks, and promotional messages, and a private, rarely disclosed one for any information you wish to keep secure. Share it only with trusted people.
- Avoid opening messages that look like spam even if they got past your filters.
- Enable two-factor authentication for your email (more on 2FA below) -- consider using your cell phone number to receive notifications about suspicious activity.
- Encrypt your email -- use a web-based email provider or set up your Outlook to use encrypted connections with GPG.
Yahoo!'s 2013 email scandal, in which all 3 billion Yahoo! email accounts were hacked, revealed that email accounts are sometimes not as well protected as you might hope.
If one of your accounts becomes hacked, that weakens all linked accounts. If hackers gain access to your email account, they may try to send a password reset email to your email address using the iCloud login system.
If you have an iCloud account associated with a Yahoo! email address, it’s best to change your password as soon as possible. Better yet, just switch mail providers. Sorry, Yahoo!. Gmail is robust.
3. Update your iPhone passcode
Your iPhone passcode is the numerical code you're prompted to use when Face ID or Touch ID aren't working. Since iOS 9, the default length for this code is six-digits, which takes considerably longer to crack than the previous four-digit default. There are 9,999 possible combinations for a 4-digit passcode, versus 999,999 combinations for a 6 digit passcode.
To increase your iPhone protection further, you can use letters in addition to numbers in your passcode. By using an alphanumeric code of more than eight letters and numbers, you can be sure that the passcode cannot be hacked or guessed -- so long you don’t use an obvious combination.
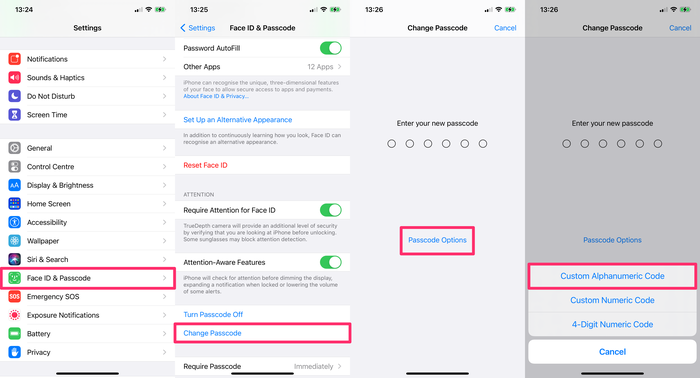
Here's how to make your iPhone passcode longer and use an alphanumeric passcode:
-
Go to
Face ID & PasscodeorTouch ID & Passcode -
Enter your current passcode
-
Tap
Change Passcode, enter your passcode again, then selectPasscode Options -
Select
Custom Alphanumeric CodeorCustom Numeric Code -
Enter your new passcode twice to reset
Make sure you remember your passcode to prevent losing your data! We recommend creating an alphanumeric passcode of 8 characters or more.
4. Use strong passwords across your accounts
While on the subject of passwords and passcodes, make sure to use secure passwords across all of your accounts.
You also need to make sure to use different passwords across all accounts, particularly when it comes to those accounts with the most valuable data. Hackers often target less protected sites, and then try these passwords out on other accounts owned by the user.
At the very least, keep your iCloud password different from the passwords you use on less secure sites, and make sure it is sufficiently complex.
When choosing a new password, aim to meet the following three criteria:
-
Strong: Use a combination of lower and upper case letters, numbers, and special characters. Replace certain letters with numbers or symbols:
beardak0tast@arhip, for example. -
Long: the longer a password is, the greater the number of combinations a hacker needs to crack it. Consider using phrases to protect the integrity of your account, which are easy for you to remember as an individual but difficult for existing software to rapidly generate. Ideal passwords are at least 14 characters long.
Hard to guess: Avoid password terms that include personal information, like your birthday, pet's name, or a favourite colour, because they're easy for hackers to guess. Don’t choose a favourite band, your birthplace, or any other relatable guess as your iCloud password. The Telegraph has written on the most commonly used passwords; they're all worth avoiding!
If you're not sure how secure your password is, there are a few free online tools to help you:
We don't recommend putting your actual password into either of them, though. Just put something in of similar complexity.
Once you've created a new password, don’t forget to save the password in a safe place. If you have a unique password for each of your accounts, it can be difficult to keep track, so you can use a password manager to compile and access your various passwords.
Tools like 1Password (paid) or KeePass (free) generate random text which generally make very strong passwords, and help you store your passwords and confidential data safely.
Back in 2016, Colin Powell and George W. Bush lost their email data after their accounts was illegally accessed by a hacker. The hacker managed to gain access by guessing the answers to their security questions. Beware!
Many common security questions ask for information that could be public knowledge. For example, many security questions ask for your mother's maiden name. This information is not exclusively known by you and could be accessed by a hacker.
To keep your account secure, use more difficult questions and answers for your security questions. Choose an alternate question, such as: “What is your favourite movie?” or “Who is your favourite author?”. Ideally, make up the answers, and record your made-up answers in a secure password manager. By using more difficult security questions, you stand a better chance of safeguarding your data.
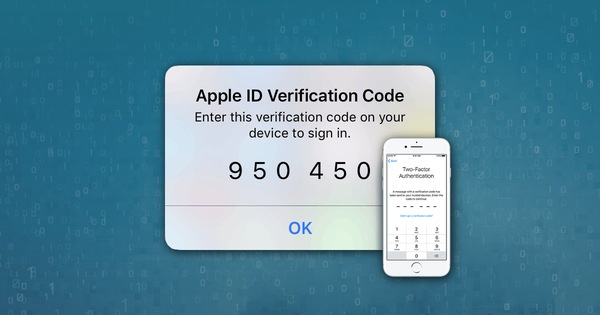
5. Activate two-factor authentication (2FA)
Two-factor authentication is an account owner verification process that is triggered whenever a new login is attempted. Apple introduced 2FA in 2016, and we at Reincubate have been providing support for this feature ever since.
2FA protects the iCloud account even where the password is known to somebody else. As long as a potential hacker doesn’t have access to any of your trusted devices, your iCloud account remains inaccessible.
Two-factor authentication works like this: when you try to login to your iCloud account, you are sent a unique code. To complete the login process, you're required to enter both your password and the code received on your phone. Without the code (randomly generated in real-time), anyone who wants to access the account won't be able to get in -- even if they have your username and password. So, hackers get locked out and you'll get a pop-up or a text message alerting you if and when they're trying to get in.
This is what you would see on an Apple device with 2FA engaged when a login from a new location is attempted:
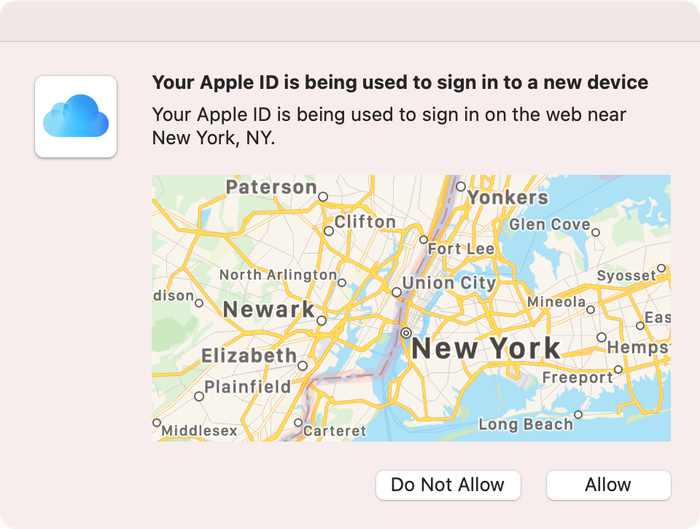
2FA is standard for all new Apple devices. If you use an Apple device that doesn't use 2FA as a default, here's how to can enable two-factor authentication for iCloud:
On your iPhone, iPad, or iPod touch with iOS 9 or later:
-
Go to
Settings -
Click on your name to access
Apple ID -
Tap
Password & Security -
Tap
Turn on Two-Factor Authentication
We cover two-factor authentication and its history in more detail in our guide here.
6. Don’t use unsecured wireless networks (and use a VPN)
Free hotspots can be a convenient way to browse the web, particularly when you're on the move. But they're not secure.
Whoever operates a network has the capability of intercepting or recording traffic sent over it. If you don't know who is running the network -- and you don't trust them -- you shouldn't use it. There's also the potential that other users of unsecured networks could attack your device and intercept your traffic or data.
The safest thing you can do is to avoid accessing the internet using these hotspots. Secured public Wi-Fi connections are safer, but you are still exposed to risks if you use them to access the cloud.
Use a good data plan with your carrier instead, and make sure your home WiFi network is secured.
If you do need Wi-Fi access on the go, invest in a Mi-Fi device, or consider using a VPN to protect your traffic. Bear in mind that using a VPN won't protect your device from other users on the network.
7. Use "Find My" to secure lost or stolen devices
Once activated, this option allows you to get in touch with your lost or stolen iPhone, or to remotely erase it. We’ve covered this in-depth here. You can essentially wipe the data on your iPhone until you recover it.
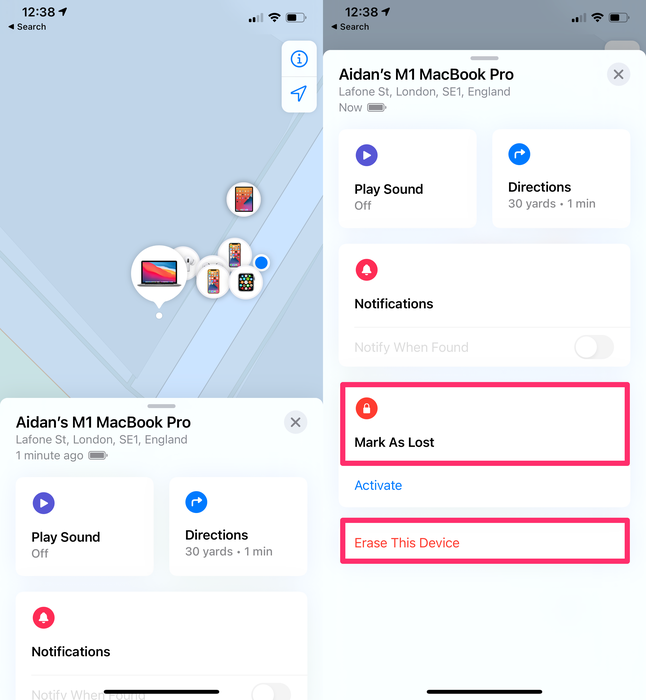
To wipe your data using "Find My":
-
Go to the
Find Myapp on a linked device -
Under
Devices, select the device that is lost or stolen. -
Select
ActivateunderMark As Lostfor that device. -
You can add a contact number to be used by anyone who finds your device.
Another benefit of this feature is that it prevents anyone else from using your iPhone if it's stolen. It can't easily be reactivated, so it's worth a lot less to a potential thief. You can also erase the data from your device using from the Find my app.
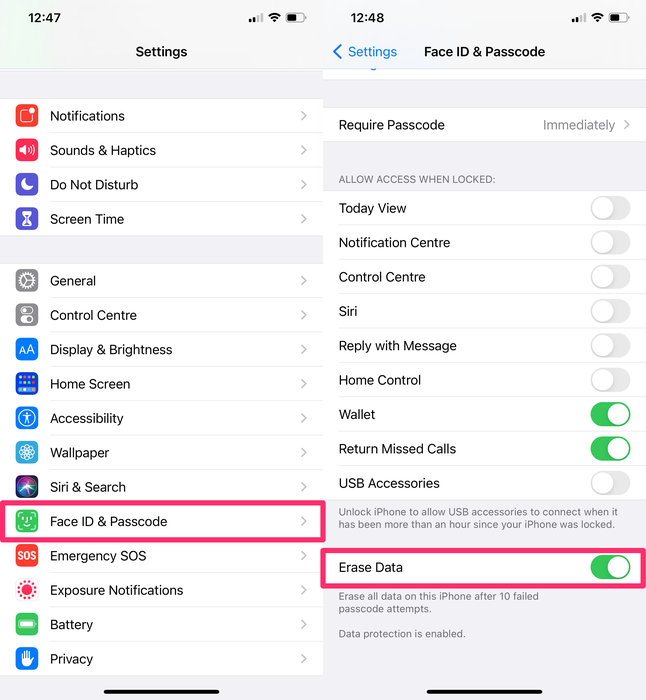
8. Enable "Erase Data" on your device
This is one of the most simple methods to prevent your phone from being attacked. If this option is enabled and somebody tries to guess your passcode, your iPhone will wipe itself after 10 failed attempts. Don't worry: this isn't something you're likely to do by accident. There's a long timeout between failed attempts. It'd take a serious attempt to have someone erase your phone.
To activate this feature:
-
Go to
Settingson your iPhone -
Tap
Face ID & PasscodeorTouch ID & Passcode -
Activate the
Erase Dataoption
9. Use local iPhone backups instead of iCloud
If you do enable "Erase Data", you should also create regular backups. An iPhone backup won't protect your data, but it will ensure that you can access your data in the event of theft or loss. iCloud backups are convenient, but they're not end-to-end encrypted, meaning it's at least theoretically possible for them to be remotely accessed.
Regular backups are so important, there’s even a World Backup Day just for them. Despite greater awareness, better habits, and easier technology, many users are still not creating regular backups.
We've written up a comprehensive guide to backing up your iPhone or iPad here.
If you're getting "iPhone Backup Failed" or "iPhone Not Backed Up" messages, your phone is not backed up, so if you lose your device, you lose your data.
10. Sign out of iCloud on unused devices and browsers
All of the devices you use iCloud with are connected in your iCloud account. Devices authorised here have low-level access to your iCloud account and all of the data in it. Hackers may attempt to gain access to your iCloud data by adding additional devices to your iCloud account.
To view and remove iCloud devices on your device:
-
Go to
Settings -
Click on your name to access
Apple ID -
Scroll down to view the devices connected in your iCloud account.
-
To remove a device, select it, then select
Remove from account -
If you find and remove any devices you do not recognise, change your iCloud password.
To view and remove iCloud devices from a browser:
-
Go to iCloud.com
-
Sign in, then go to
Settings -
Select
My Devices -
Remove any devices you don't recognise or no longer use.
-
If you find and remove any devices you do not recognise, change your iCloud password.
Once you've removed a device, you will no longer be able to use "Find my" to locate it.
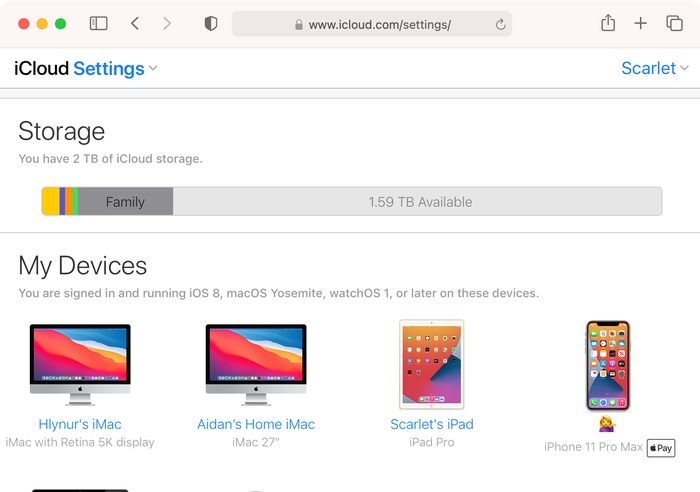
In addition to removing unused iCloud devices, you should also make sure to log out of your iCloud account when using a shared browser.
If you logged in to iCloud on a computer that is not your own (such as a work computer or friend’s computer) and forgot to log out, you can log out remotely.
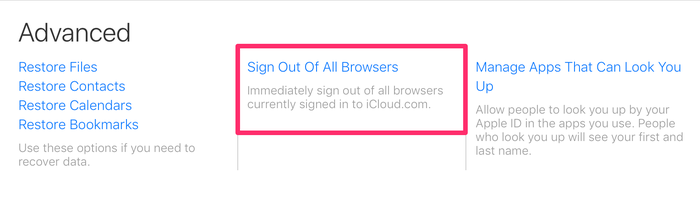
To sign out of iCloud remotely:
-
Go to iCloud.com and log in with your username and password.
-
Select
Account Settings -
Scroll to the bottom of the screen to find the link that says
Sign Out Of All Browsers -
Click it and you'll be signed out of all browsers on any device anywhere in the world where you are signed in to your iCloud account
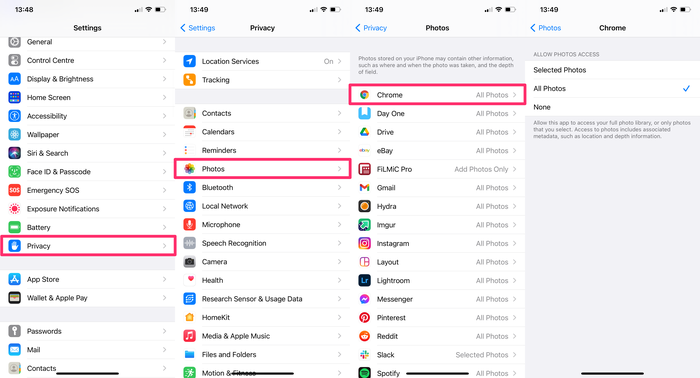
11. Turn off access to sensitive data for apps that don’t need it
To keep your data private you can also restrict access to apps that don’t need it, for example, access to your contacts, calendar, photos, etc.
To restrict access for apps on your device:
-
Go to
Settings -
Select
Privacy -
Select one of the apps listed, such as
Photos
Here, you can view the apps that currently have access to this data. Toggle the switch on the right to remove access to data for each app.
12. Secure your lock screen
Contrary to popular belief, Touch ID and Face ID do not make your iPhone completely unhackable. Shortly after Apple launched FaceID, cybersecurity firm Bkav created a printed mask capable of unlocking an iPhone X.
Lockscreen attacks via Touch ID, Face ID or your iPhone passcode, aren't very common, as they require the hacker to have direct physical contact with your phone, but they’re the easiest attack to attempt and most likely to succeed if your device is not configured correctly.
To secure your lock screen, remove access to functions and controls when the phone is locked. If you allow access to USB accessories when your phone is locked, a hacker could simply connect your phone to their computer and download your data. Similarly, if they can access Siri, they could gain access to your messages.
The best protection from physical attacks on your iPhone is to remove access to various controls and functions from the lock screen.
To deactivate access from the lock screen:
-
Go to
Settings -
Select
Face ID and PasscodeorTouch ID and Passcode -
Enter your iPhone passcode
-
Scroll down to the bottom of the screen and disable access to Control Centre
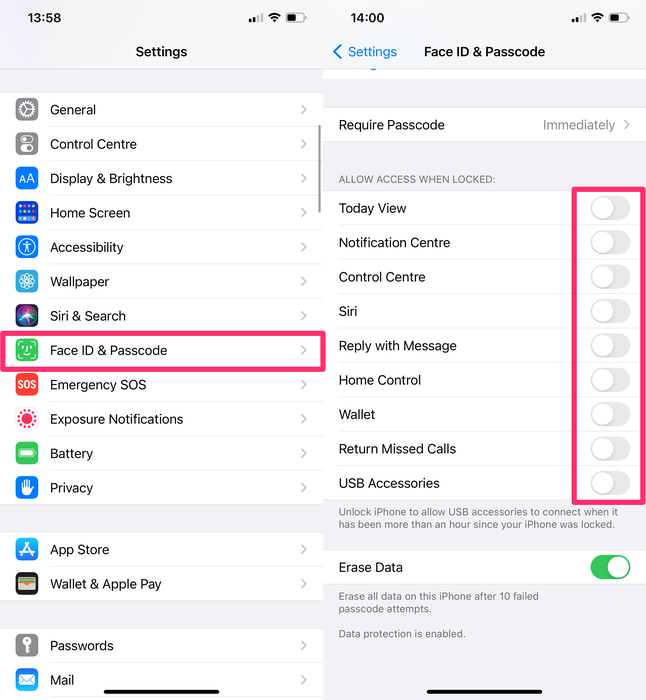
We've disabled access to all controls from the lock screen because that's the safest approach. At a minimum, we recommend you remove lock screen access to all of the following:
-
Today View
-
Notification Centre
-
Control Centre
-
Siri
-
Reply with Message
-
Home Control
-
USB Accessories
Five more security measures you might want to implement
If you're particularly concerned about the privacy and security of your data, you can use the following five security measures to further protect your data and devices.
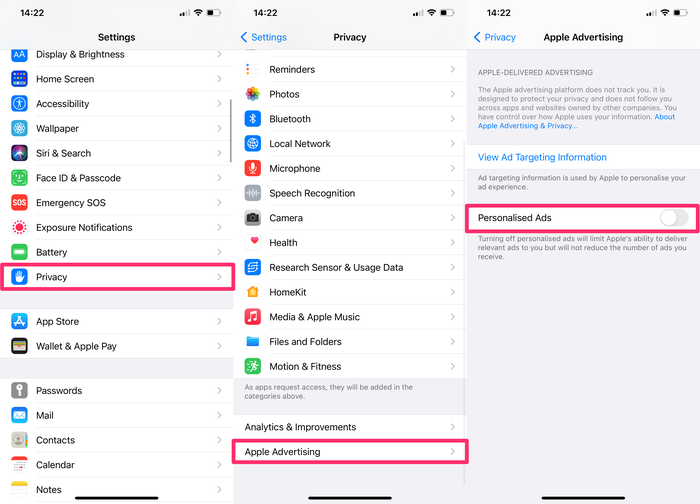
1. Turn off "Personalised Ads"
Ad tracking is used by advertising networks to target ads to you. If you limit this, it restricts tracking of ads across apps. Well, apart from when Google bypass it.
To limit ad tracking on your iOS device:
-
Go to
Settings -
Select
Privacy -
Scroll to the bottom of the screen and select
Advertising -
Toggle to turn off
Personalised Ads
You can also Reset Advertising Identifier to remove the history of the data already compiled and used to send you targeted advertisements.
2. If you're a macOS user, consider pair-locking your iPhone
Pair-locking requires a little technical knowledge and isn't for everyone, so we've covered it in more detail in another article. In short, it prevents your iPhone from ever exchanging data with another computer.
3. Delete unwanted or sensitive content from Photo Stream or iCloud Photo library
If you have any particularly confidential content in your photo library, it might make sense to not store it on your smartphone at all. If you delete a sensitive image, ensure you remove it from "Deleted items", too. Be aware of all the ways this data can be recovered.
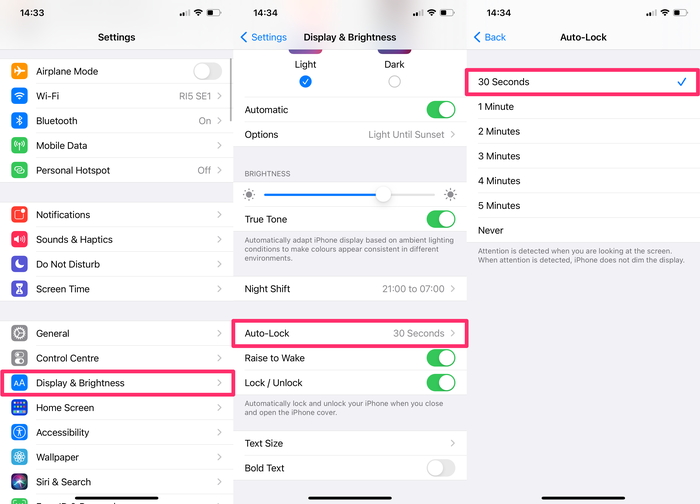
4. Decrease the time until the iPhone locks itself
iPhones get snatched on the street every now and then. When that happens, the iPhone is usually unlocked, and the thief will have access to everything.
To prevent this, use a shorter time interval for automatic iPhone locking. To decrease the number of seconds until the phone lock screen is activated you need to change the Auto-Lock timer’s settings.
To decrease your phone's lock time:
-
Go to
Settings -
Scroll down and select
Display & Brightness -
Select
Auto-Lockand adjust the time available until the iPhone is locked.
The shortest interval of time is 30 seconds. Activate this option and confirm the action.
5. Encrypt your locally saved data
If you have sensitive data on your computer, it’s best to encrypt it. Windows has BitLocker built into it, and Macs have FileVault. Both are great -- and free to use. Turn them on.
If your computer is stolen and it has an encrypted disk, you can make an insurance claim and forget about it, assuming you had a strong password. It's nice not to worry about someone accessing your data. Don't risk it!
Conclusion
We've covered the most important security features to restrict unauthorised iPhone or iCloud access. As new tools are developed by hackers and forensics companies the risks increase, making security an ongoing battle.
As a company, data privacy and security are in our DNA. We built iPhone Backup Extractor to be compatible with all of Apple's security measures, and we're committed to ensuring our product is used by legitimate, ethical users. Stay safe!